What is PHP Code Injection ?
Code injection is a technique used by attacker to inject server-side code from outside so that it can be evaluated by the corresponding server-side technology.
Code injection allows an attacker to compromise database, security, it is also possible to steal data, bypass access and authentication control. This vulnerability can be easy to find or sometimes it may be harder to find.
What Can Be Done By Code Injection ?
Code injection attacks are very serious as it leads to compromising application's data and functionality, also it can gather information about the server that is hosting the application. It is even possible to use the server as a platform to attack other systems.
Code injection capabilities are limited by the functionalities of the language used for the attack. For example, if PHP is used for this purpose, the attack has all the capabilities same as PHP.
Important Note
Please note that, all the information provided in this post is solely meant for educational purposes only.
How Does Code Injection Work ?
Generally, web applications are vulnerable to this attack when code is executed without proper input validation.
How To Use Code Injection ?
Let's see how we can use PHP code injection. For this purpose, we will create a forgot password page, that is vulnerable to code injection.Following is the screen-shot for adding the forgot password link.
 |
| Forgot Password Added Codes |
Screen shot of forgot password page.
 |
| Forgot Password Page |
Getting The Complete PHP Configurations Of The Server
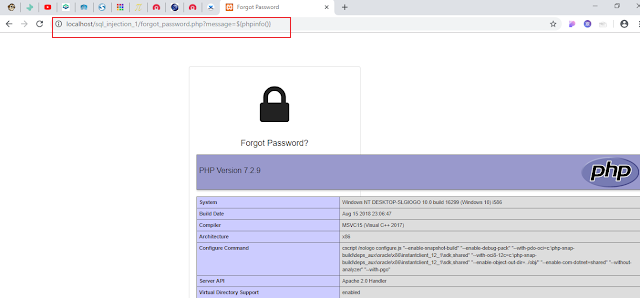 |
| Getting Complete PHP Configurations Of The Server |
 | |
|
From the screen shot above, you can see a red rectangle area, that displays the root directory location of the server.
Next, we will look at how an attacker can use this information to create a new file in the application's root directory.
 |
| Creating a New File In The Server's Root Directory |
Download the entire project by clicking below
Explanation
In the screen shot above, the attacker uses php's fwrite function to create a text file named "attacker.txt" in root location of application. The error suppression operator "@" is used to ignore error messages that might be generated while fwrite is executed.After successful execution, you will see a text file attacker.txt is generated, similar to the screen shot shown below.
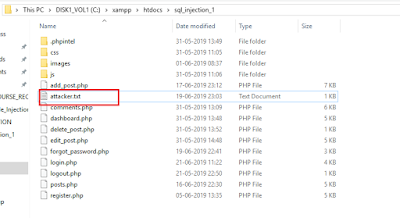 |
| Created attacker.txt file in server's root directory |
How To Prevent PHP Code Injection ?
To protect against php code injection, we will use htmlspecialchars() function which allows to convert html characters to html entities. For example, "&" will be treated as "&". So, the code injection attack will not work anymore.
Make, following changes marked in red rectangle in forgot_password.php file as shown below in the screen shot.
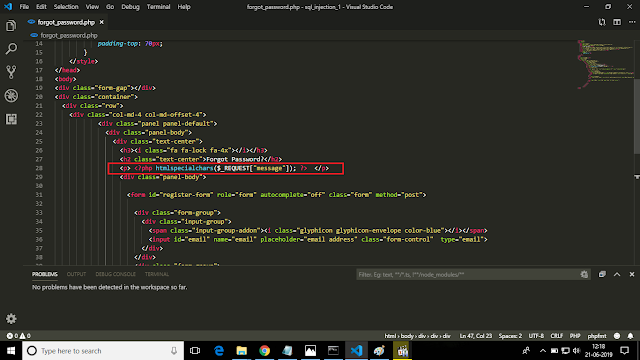 |
| Protecting Against PHP Code Injection |
After making that change, if we try to do code injection, we won't see any effect of it. So we successfully, prevented that attack. You will see something like the following screen shot if you, do the same.
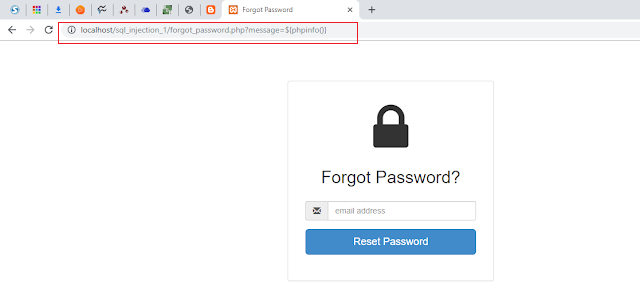 |
| Protecting Against PHP Code Injection Output |









No comments:
Post a Comment